List of Algorithms. A complete list of all major algorithms 3. The goal. is to provide a ready to run program for each one, or a description of the. Programming languages include Java, Java. Script and PHP, C, C. Scriptol source. Automata. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. The calculation result in that the program equals the manual computation result, proving that the program is correct. 4. Simulation of the Fracture Network. C Program To Generate Line Using Dda Algorithm CPowerset construction. Algorithm to convert nondeterministic. Todd Coxeter algorithm. Procedure for generating cosets. Artificial intelligence. Alpha beta. Alpha max plus beta min. Basic algo used to find the best move in board. Ant algorithms. The ant colony optimisation is a set of algorithms inspired by ant behavior to solve a problem, find the best path between two locations. Together with Vlad Tenev, secondgeneration American Baiju Bhatt founded the stock brokerage service Robinhood, which lets users trade public stocks from their mobile. Do I need to know calculus or complex math to program a SpeedoHealer like I hear your competitor claim 8. Fix Your WiFi Signal. If youre using WiFi, you might find that your router and internet are fine, but your wireless signal is weak, causing a slowdown. Gmail is email thats intuitive, efficient, and useful. 15 GB of storage, less spam, and mobile access.  CLA. Cortical Learning Algorithm. For robotic learning, based on three properties, sparse distributed representation, temporal inference, on linelearning. Code available through the Nu. Pic project from Numenta. DE Differential evolution. Solve the Chebyshev. Semi Supervised Recognition of Sarcastic Sentences in Online Product Reviews. Algorithm that recognize sacarsms or irony in a tweet or an online document. A such algorithm will be essential for humanoid robots programming too. Sentiment analysis. Actually a combination of algos, naive Bayes, maximum entropy and SVM Support Vector Machine classifieur. Computer vision. Epitome. Represent an image or video by a smaller one. Counting objects in an image. Uses the connected component. Deep Dense Face Detector. Farafade, Saberian and Li. Able to recognize face even with different angles. Evolution Constructed Features. Brigham Young University. For the ability to identify known objects and add new objects to the knowledge base without human intervention. OCarroll algorithm. From a mathematical conversion of insect vision, this algorithm evaluates how to get around avoiding objects. Tracking Learning Detection. Detects moving objects and follows them. Viola Jones object detection framework, simple and fast. Able to recognize human faces, it is implemented in Open. CV. Genetic algorithms. They uses three operator. Fitness proportionate selection. Also known as roulette wheel. Truncation selection. Another method for selecting solutions. Tournament selection. Select the best solution by a kind. Stochastic universal sampling. The individuals are mapped. Neural networks. Hopfield net. Recurrent artificial neural network that. They converge to a stable state. Backpropagation. Supervised learning technique used for. Self organizing map Kohonen map. Neural networks trained. D, 3. D. representation of the training samples. Good for visualizing high dimensional. Machine learning. PAVA Pool Adjacent Violators Algorithm. Leeuw, Hornik, Mair. Improve a function for a set of points. Optimize the isotonic regression. C code. Multiplicative Weights. Assigns weights to different strategy to make a decision. This applies to objects recognition and is found also in natural genetics. Bioinformatics and Cheminformatics. Needleman Wunsch. Performs a global alignment on two sequences. Smith Waterman. Variation of the Needleman Wunsch. Ullmanns algorithm for subgraph isomorphism solving. Determine if two graphs have isomorphic subgraphs. The maximum common subgraph isomorphism problem may be computed with a modular product graph. Compression. Lossless compression algorithms. Burrows Wheeler transform. Preprocessing useful for improving. Deflate. Data compression used by ZIP. Delta encoding. Aid to compression of data in which sequential. Incremental encoding. Delta encoding applied to sequences. LZW. Lempel Ziv Welch. Successor of LZ7. Builds a translation. Is used by the GIF graphical format. LZ7. 7 and 7. 8. The basis of further LZ variations LZW, LZSS. They are both dictionary coders. LZMA. Short for Lempel Ziv Markov chain Algorithm. LZO. Data compression algorithm that is focused on speed. PPM Prediction by Partial Matching. Adaptive statistical. Shannon Fano coding. Constructs prefix codes based on a. Truncated binary. An entropy encoding typically used for. Improve. binary encoding. Run length encoding. Primary compression that replaces. Sequitur. Incremental grammar inference on a string. EZW Embedded Zerotree Wavelet. Progressive encoding to. May. be lossy compression also with better results. Zopfli. By Google, generic compression, efficient but slow. The name means small bread in swiss german. Brotli. By Google, successor to Zopfli but faster, based on LZ 7. Entropy encoding Coding scheme that assigns codes to symbols so as to match code. Huffman coding. Simple lossless compression taking advantage. Adaptive Huffman coding. Adaptive coding technique based. Huffman coding. Arithmetic coding. Advanced entropy coding. Range encoding. Same as arithmetic coding, but looked. Unary coding. Code that represents a number n with n. Elias delta, gamma, omega coding. Universal. code encoding the positive integers. Fibonacci coding. Universal code which encodes positive. Golomb coding. Form of entropy coding that is optimal. Rice coding. Form of entropy coding that is optimal for. Lossy compression algorithms. Linear predictive coding. Lossy compression by representing. A law algorithm. Standard companding algorithm. Mu law algorithm. Standard analog signal compression or. Fractal compression. Method used to compress images using. Transform coding. Type of data compression for data like. Vector quantization. Technique often used in lossy data. Wavelet compression. Form of data compression well suited. Cryptography. Secret key symmetric encryption. Use a secret key or a pair of directly related keys for both decryption. Advanced Encryption Standard AES, also known as Rijndael. Blowfish. Designed by Schneier as a general purpose algorithm. DE. Data Encryption Standard DES, formerly DE Algorithm. IDEA International Data Encryption Algorithm. Formerly. IPES Improved PES, another replacement for DES. Is used by PGP. Pretty Good Privacy. Performs transformations on data splitted. RC4 or ARC4. Stream cipher widely used in protocols such. SSL for Internet traffic and WEP for wireless networks. Tiny Encryption. Algorithm. Easy to implement block cipher algorithme. PES Proposed Encryption Standard. Older name for IDEA. Public key asymmetric encryption. Use a pair of keys, designated as public key and private key. The public. key encrypt the message, only the private key permits to decrypt it. DSA Digital Signature Algorithm. Generate keys with prime. Was used by US agencies, and now public domain. El. Gamal. Based on Diffie Hellman, used by GNU Privacy Guard. PGP, and other cryptographic systems. RSA Rivest, Shamir, Adleman. Widely used in electronic. Use prime numbers. Diffie Hellman Merkle key exchange or exponential key. Method and algorithm to share secret over an unprotected. Used by RSA. NTRUEncrypt. Make use of rings of polynomials with convolution. Message digest functions. A message digest is a code resulting of the encryption of a string or. MD5. Used for checking ISO images of CDs or DVDs. RIPEMD RACE Integrity Primitives Evaluation Message Digest. Based upon the principles of MD4 and similar to SHA 1. SHA 1 Secure Hash Algorithm 1. Most commonly used. SHA set of related cryptographic hash functions. Was designed. by the NSA agency. HMAC. keyed hash message authentication. Tiger TTH. Usually used in Tiger tree hashes. Cryptographic using pseudo random numbers. Techniques in cryptography. Secret sharing, Secret Splitting, Key Splitting, M of N algorithms. Shamirs secret sharing scheme. This is a formula based. Blakleys secret sharing scheme. Is geometric in nature. Other techniques and decryption Subset sum. Libro Wikipedia, la enciclopedia libre. Un libro del latnliber, libri es una obra impresa, manuscrita o pintada en una serie de hojas de papel, pergamino, vitela u otro material, unidas por un lado es decir, encuadernadas y protegidas con tapas, tambin llamadas cubiertas. Un libro puede tratar sobre cualquier tema. Segn la definicin de la Unesco,1 un libro debe poseer 2. Tambin se llama libro a una obra de gran extensin publicada en varias unidades independientes, llamados tomos o volmenes. Otras veces se llama tambin libro a cada una de las partes de una obra, aunque fsicamente se publiquen todas en un mismo volumen ejemplo Libros de la Biblia. Hoy en da, no obstante, esta definicin no queda circunscrita al mundo impreso o de los soportes fsicos, dada la aparicin y auge de los nuevos formatos documentales y especialmente de la World Wide Web. El libro digital o libro electrnico, conocido como e book, est viendo incrementado su uso en el mundo del libro y en la prctica profesional bibliotecaria y documental. Adems, el libro tambin puede encontrarse en formato audio, en cuyo caso se denomina audiolibro. Desde los orgenes, la humanidad ha tenido que hacer frente a una cuestin fundamental la forma de preservar y transmitir su cultura, es decir, sus creencias y conocimientos, tanto en el espacio como en el tiempo. El planteamiento de esta cuestin supone por un lado, determinar la forma de garantizar la integridad intelectual del contenido de la obra y la conservacin del soporte en el que fue plasmada, y por otro, encontrar el medio por el cual se mantendr inalterada la intencin o finalidad para la cual se concibi. Los orgenes de la historia del libro se remontan a las primeras manifestaciones pictricas de nuestros antepasados, la pintura rupestre del hombre del paleoltico. Con un simbolismo, posiblemente cargado de significados mgicos, estas pinturas muestran animales, caceras y otras escenas cotidianas del entorno natural del hombre antiguo, que trataba de dominar las fuerzas adversas de la naturaleza capturando su esencia mediante su representacin. Son el ms antiguo precedente de los primeros documentos impresos de que se tiene memoria. Comunicacin oral y formas rudimentariaseditarLas seales gestuales fueron la primera forma de expresar y transmitir mensajes. La palabra hablada es la manera ms antigua de contar historias. Mediante frmulas de valor mnemotcnico2 se estructuraban narraciones, que pasaban de generacin en generacin como valiosa herencia cultural de los ms diversos grupos humanos. Dichas reglas mnemotcnicas ayudaban tanto a la memorizacin como a la difusin de los relatos. Es el caso de los poemas homricos, que han merecido valiosos estudios sobre el particular. Posiblemente, gran parte de las tradiciones y leyendas han tenido semejante inicio. Esta transmisin oral tena el inconveniente de los ruidos que deformaban el mensaje. La mayora de las veces era el narrador rapsoda, aeda, juglar quien en funcin de sus intereses la deformaba de una u otra forma. La escrituraeditarCuando los sistemas de escritura fueron inventados en las antiguas civilizaciones, el hombre utiliz diversos soportes de escritura tablillas de arcilla, ostracon, placas de hueso o marfil, tablas de madera, papiros, tablillas enceradas, planchas de plomo, pieles curtidas, etc. La escritura fue el resultado de un proceso lento de evolucin con diversos pasos imgenes que reproducan objetos cotidianos pictografa representacin mediante smbolos ideografa y la reproduccin de slabas y letras. Los ms antiguos vestigios de escritura se encuentran, hacia finales del IV milenio a. C., en el Antiguo Egipto, con jeroglficos, y la antigua Mesopotamia, mediante signos cuneiformes escritura cuneiforme utilizaban una varilla con seccin triangular, que al hendir en placas de arcilla, dejaba una marca en forma de cua. La usaron los sumerios, acadios, asirios, hititas, persas, babilonios etc. La escritura egipcia, que perdur ms de tres milenios, mediante jeroglficos, representaba ideas abstractas, objetos, palabras, slabas, letras y nmeros. Evolucion en las escrituras hiertica y demtica. Otros pueblos, como los hititas y los aztecas tambin tuvieron tipos propios de escritura. La escritura china ms antigua que se conoce son 5. C. en el yacimiento de Xiaotun, en la provincia de Henan. Pero los primeros libros reconocibles de China corresponden al siglo VI a. C., los jiance o jiandu, rollos de finas tiras de bamb o madera grabados con tinta indeleble y atados con cordel. Estos textos servan principalmente a causas institucionales, era la obra de funcionarios civiles o militares. 3Desde Confucio en adelante 5. C. los libros se convirtieron en importantes instrumentos de aprendizaje, se escribieron tratados de filosofa, medicina, astronoma y cartografa. En el perodo de los reinos combatientes 4. C. La seda se us mucho como soporte para escribir. La tela era ligera, resistente al clima hmedo, absorba bien la tinta y proporcionaba al texto un fondo blanco, sin embargo era mucho ms cara que el bamb, es por esto que en ocasiones se haca una copia en bamb antes de grabarse en seda los textos importantes. La invencin del papel segn la tradicin china, se atribuye a un eunuco de la corte imperial llamado Cai Lin en el 1. C. Usando nuevos ingredientes trapos viejos, camo, corteza de rbol y redes de pescar cre un mtodo de fabricacin de papel muy similar al que se usa hoy en da. Pero el papel tard cientos de aos en reemplazar al bamb y la seda, fue hasta finales del siglo II d. C. que la corte imperial lo us en cantidades importantes. Esta innovacin no se propag fuera de China hasta el 6. C. aproximadamente, y alcanz Europa a travs de Espaa hasta el siglo XII. A mediados del siglo VIII los chinos inventaron la impresin xilogrfica, o el grabado en madera, y la necesidad de reproducir un gran nmero de textos e imgenes budistas, calendarios, manuales de adivinacin y diccionarios promovi una rpida y temprana propagacin de la xilografa. El primer libro impreso chino que se ha encontrado es el Sutra del diamante del 8. C. Los impresores chinos crearon los tipos mviles hacia el siglo XI, el escritor chino Chen Kua 1. Mengshi Pitan, segn el escritor el herrero Jen. Tsung de la dinasta de los Song del norte entre 1. Tambin se le atribuye la creacin de una mesa giratoria para guardar los caracteres, esta tcnica se llamaba tipografa tablearia. Hacia el 1. 30. 0 Wang Tcheng, un tcnico agrnomo, emplaz la arcilla por madera de azufaifo, que era mucho ms dura. Pero este avance no revolucion la imprenta hasta el punto que lo hizo Gutenberg en Europa 4. A diferencia de las lenguas europeas, el chino escrito requiere miles de caracteres nicos, lo que hace mucho ms eficaz los bloques de madera individuales que los enormes conjuntos de tipos reutilizables. En contraste con el declive de las artes de los escribas en occidente en los siglos que siguieron a la creacin de la imprenta de tipos mviles, la caligrafa china conserv su prestigio, era un arte. No obstante, a finales del siglo XV, China haba producido ms libros que el resto del mundo junto.
CLA. Cortical Learning Algorithm. For robotic learning, based on three properties, sparse distributed representation, temporal inference, on linelearning. Code available through the Nu. Pic project from Numenta. DE Differential evolution. Solve the Chebyshev. Semi Supervised Recognition of Sarcastic Sentences in Online Product Reviews. Algorithm that recognize sacarsms or irony in a tweet or an online document. A such algorithm will be essential for humanoid robots programming too. Sentiment analysis. Actually a combination of algos, naive Bayes, maximum entropy and SVM Support Vector Machine classifieur. Computer vision. Epitome. Represent an image or video by a smaller one. Counting objects in an image. Uses the connected component. Deep Dense Face Detector. Farafade, Saberian and Li. Able to recognize face even with different angles. Evolution Constructed Features. Brigham Young University. For the ability to identify known objects and add new objects to the knowledge base without human intervention. OCarroll algorithm. From a mathematical conversion of insect vision, this algorithm evaluates how to get around avoiding objects. Tracking Learning Detection. Detects moving objects and follows them. Viola Jones object detection framework, simple and fast. Able to recognize human faces, it is implemented in Open. CV. Genetic algorithms. They uses three operator. Fitness proportionate selection. Also known as roulette wheel. Truncation selection. Another method for selecting solutions. Tournament selection. Select the best solution by a kind. Stochastic universal sampling. The individuals are mapped. Neural networks. Hopfield net. Recurrent artificial neural network that. They converge to a stable state. Backpropagation. Supervised learning technique used for. Self organizing map Kohonen map. Neural networks trained. D, 3. D. representation of the training samples. Good for visualizing high dimensional. Machine learning. PAVA Pool Adjacent Violators Algorithm. Leeuw, Hornik, Mair. Improve a function for a set of points. Optimize the isotonic regression. C code. Multiplicative Weights. Assigns weights to different strategy to make a decision. This applies to objects recognition and is found also in natural genetics. Bioinformatics and Cheminformatics. Needleman Wunsch. Performs a global alignment on two sequences. Smith Waterman. Variation of the Needleman Wunsch. Ullmanns algorithm for subgraph isomorphism solving. Determine if two graphs have isomorphic subgraphs. The maximum common subgraph isomorphism problem may be computed with a modular product graph. Compression. Lossless compression algorithms. Burrows Wheeler transform. Preprocessing useful for improving. Deflate. Data compression used by ZIP. Delta encoding. Aid to compression of data in which sequential. Incremental encoding. Delta encoding applied to sequences. LZW. Lempel Ziv Welch. Successor of LZ7. Builds a translation. Is used by the GIF graphical format. LZ7. 7 and 7. 8. The basis of further LZ variations LZW, LZSS. They are both dictionary coders. LZMA. Short for Lempel Ziv Markov chain Algorithm. LZO. Data compression algorithm that is focused on speed. PPM Prediction by Partial Matching. Adaptive statistical. Shannon Fano coding. Constructs prefix codes based on a. Truncated binary. An entropy encoding typically used for. Improve. binary encoding. Run length encoding. Primary compression that replaces. Sequitur. Incremental grammar inference on a string. EZW Embedded Zerotree Wavelet. Progressive encoding to. May. be lossy compression also with better results. Zopfli. By Google, generic compression, efficient but slow. The name means small bread in swiss german. Brotli. By Google, successor to Zopfli but faster, based on LZ 7. Entropy encoding Coding scheme that assigns codes to symbols so as to match code. Huffman coding. Simple lossless compression taking advantage. Adaptive Huffman coding. Adaptive coding technique based. Huffman coding. Arithmetic coding. Advanced entropy coding. Range encoding. Same as arithmetic coding, but looked. Unary coding. Code that represents a number n with n. Elias delta, gamma, omega coding. Universal. code encoding the positive integers. Fibonacci coding. Universal code which encodes positive. Golomb coding. Form of entropy coding that is optimal. Rice coding. Form of entropy coding that is optimal for. Lossy compression algorithms. Linear predictive coding. Lossy compression by representing. A law algorithm. Standard companding algorithm. Mu law algorithm. Standard analog signal compression or. Fractal compression. Method used to compress images using. Transform coding. Type of data compression for data like. Vector quantization. Technique often used in lossy data. Wavelet compression. Form of data compression well suited. Cryptography. Secret key symmetric encryption. Use a secret key or a pair of directly related keys for both decryption. Advanced Encryption Standard AES, also known as Rijndael. Blowfish. Designed by Schneier as a general purpose algorithm. DE. Data Encryption Standard DES, formerly DE Algorithm. IDEA International Data Encryption Algorithm. Formerly. IPES Improved PES, another replacement for DES. Is used by PGP. Pretty Good Privacy. Performs transformations on data splitted. RC4 or ARC4. Stream cipher widely used in protocols such. SSL for Internet traffic and WEP for wireless networks. Tiny Encryption. Algorithm. Easy to implement block cipher algorithme. PES Proposed Encryption Standard. Older name for IDEA. Public key asymmetric encryption. Use a pair of keys, designated as public key and private key. The public. key encrypt the message, only the private key permits to decrypt it. DSA Digital Signature Algorithm. Generate keys with prime. Was used by US agencies, and now public domain. El. Gamal. Based on Diffie Hellman, used by GNU Privacy Guard. PGP, and other cryptographic systems. RSA Rivest, Shamir, Adleman. Widely used in electronic. Use prime numbers. Diffie Hellman Merkle key exchange or exponential key. Method and algorithm to share secret over an unprotected. Used by RSA. NTRUEncrypt. Make use of rings of polynomials with convolution. Message digest functions. A message digest is a code resulting of the encryption of a string or. MD5. Used for checking ISO images of CDs or DVDs. RIPEMD RACE Integrity Primitives Evaluation Message Digest. Based upon the principles of MD4 and similar to SHA 1. SHA 1 Secure Hash Algorithm 1. Most commonly used. SHA set of related cryptographic hash functions. Was designed. by the NSA agency. HMAC. keyed hash message authentication. Tiger TTH. Usually used in Tiger tree hashes. Cryptographic using pseudo random numbers. Techniques in cryptography. Secret sharing, Secret Splitting, Key Splitting, M of N algorithms. Shamirs secret sharing scheme. This is a formula based. Blakleys secret sharing scheme. Is geometric in nature. Other techniques and decryption Subset sum. Libro Wikipedia, la enciclopedia libre. Un libro del latnliber, libri es una obra impresa, manuscrita o pintada en una serie de hojas de papel, pergamino, vitela u otro material, unidas por un lado es decir, encuadernadas y protegidas con tapas, tambin llamadas cubiertas. Un libro puede tratar sobre cualquier tema. Segn la definicin de la Unesco,1 un libro debe poseer 2. Tambin se llama libro a una obra de gran extensin publicada en varias unidades independientes, llamados tomos o volmenes. Otras veces se llama tambin libro a cada una de las partes de una obra, aunque fsicamente se publiquen todas en un mismo volumen ejemplo Libros de la Biblia. Hoy en da, no obstante, esta definicin no queda circunscrita al mundo impreso o de los soportes fsicos, dada la aparicin y auge de los nuevos formatos documentales y especialmente de la World Wide Web. El libro digital o libro electrnico, conocido como e book, est viendo incrementado su uso en el mundo del libro y en la prctica profesional bibliotecaria y documental. Adems, el libro tambin puede encontrarse en formato audio, en cuyo caso se denomina audiolibro. Desde los orgenes, la humanidad ha tenido que hacer frente a una cuestin fundamental la forma de preservar y transmitir su cultura, es decir, sus creencias y conocimientos, tanto en el espacio como en el tiempo. El planteamiento de esta cuestin supone por un lado, determinar la forma de garantizar la integridad intelectual del contenido de la obra y la conservacin del soporte en el que fue plasmada, y por otro, encontrar el medio por el cual se mantendr inalterada la intencin o finalidad para la cual se concibi. Los orgenes de la historia del libro se remontan a las primeras manifestaciones pictricas de nuestros antepasados, la pintura rupestre del hombre del paleoltico. Con un simbolismo, posiblemente cargado de significados mgicos, estas pinturas muestran animales, caceras y otras escenas cotidianas del entorno natural del hombre antiguo, que trataba de dominar las fuerzas adversas de la naturaleza capturando su esencia mediante su representacin. Son el ms antiguo precedente de los primeros documentos impresos de que se tiene memoria. Comunicacin oral y formas rudimentariaseditarLas seales gestuales fueron la primera forma de expresar y transmitir mensajes. La palabra hablada es la manera ms antigua de contar historias. Mediante frmulas de valor mnemotcnico2 se estructuraban narraciones, que pasaban de generacin en generacin como valiosa herencia cultural de los ms diversos grupos humanos. Dichas reglas mnemotcnicas ayudaban tanto a la memorizacin como a la difusin de los relatos. Es el caso de los poemas homricos, que han merecido valiosos estudios sobre el particular. Posiblemente, gran parte de las tradiciones y leyendas han tenido semejante inicio. Esta transmisin oral tena el inconveniente de los ruidos que deformaban el mensaje. La mayora de las veces era el narrador rapsoda, aeda, juglar quien en funcin de sus intereses la deformaba de una u otra forma. La escrituraeditarCuando los sistemas de escritura fueron inventados en las antiguas civilizaciones, el hombre utiliz diversos soportes de escritura tablillas de arcilla, ostracon, placas de hueso o marfil, tablas de madera, papiros, tablillas enceradas, planchas de plomo, pieles curtidas, etc. La escritura fue el resultado de un proceso lento de evolucin con diversos pasos imgenes que reproducan objetos cotidianos pictografa representacin mediante smbolos ideografa y la reproduccin de slabas y letras. Los ms antiguos vestigios de escritura se encuentran, hacia finales del IV milenio a. C., en el Antiguo Egipto, con jeroglficos, y la antigua Mesopotamia, mediante signos cuneiformes escritura cuneiforme utilizaban una varilla con seccin triangular, que al hendir en placas de arcilla, dejaba una marca en forma de cua. La usaron los sumerios, acadios, asirios, hititas, persas, babilonios etc. La escritura egipcia, que perdur ms de tres milenios, mediante jeroglficos, representaba ideas abstractas, objetos, palabras, slabas, letras y nmeros. Evolucion en las escrituras hiertica y demtica. Otros pueblos, como los hititas y los aztecas tambin tuvieron tipos propios de escritura. La escritura china ms antigua que se conoce son 5. C. en el yacimiento de Xiaotun, en la provincia de Henan. Pero los primeros libros reconocibles de China corresponden al siglo VI a. C., los jiance o jiandu, rollos de finas tiras de bamb o madera grabados con tinta indeleble y atados con cordel. Estos textos servan principalmente a causas institucionales, era la obra de funcionarios civiles o militares. 3Desde Confucio en adelante 5. C. los libros se convirtieron en importantes instrumentos de aprendizaje, se escribieron tratados de filosofa, medicina, astronoma y cartografa. En el perodo de los reinos combatientes 4. C. La seda se us mucho como soporte para escribir. La tela era ligera, resistente al clima hmedo, absorba bien la tinta y proporcionaba al texto un fondo blanco, sin embargo era mucho ms cara que el bamb, es por esto que en ocasiones se haca una copia en bamb antes de grabarse en seda los textos importantes. La invencin del papel segn la tradicin china, se atribuye a un eunuco de la corte imperial llamado Cai Lin en el 1. C. Usando nuevos ingredientes trapos viejos, camo, corteza de rbol y redes de pescar cre un mtodo de fabricacin de papel muy similar al que se usa hoy en da. Pero el papel tard cientos de aos en reemplazar al bamb y la seda, fue hasta finales del siglo II d. C. que la corte imperial lo us en cantidades importantes. Esta innovacin no se propag fuera de China hasta el 6. C. aproximadamente, y alcanz Europa a travs de Espaa hasta el siglo XII. A mediados del siglo VIII los chinos inventaron la impresin xilogrfica, o el grabado en madera, y la necesidad de reproducir un gran nmero de textos e imgenes budistas, calendarios, manuales de adivinacin y diccionarios promovi una rpida y temprana propagacin de la xilografa. El primer libro impreso chino que se ha encontrado es el Sutra del diamante del 8. C. Los impresores chinos crearon los tipos mviles hacia el siglo XI, el escritor chino Chen Kua 1. Mengshi Pitan, segn el escritor el herrero Jen. Tsung de la dinasta de los Song del norte entre 1. Tambin se le atribuye la creacin de una mesa giratoria para guardar los caracteres, esta tcnica se llamaba tipografa tablearia. Hacia el 1. 30. 0 Wang Tcheng, un tcnico agrnomo, emplaz la arcilla por madera de azufaifo, que era mucho ms dura. Pero este avance no revolucion la imprenta hasta el punto que lo hizo Gutenberg en Europa 4. A diferencia de las lenguas europeas, el chino escrito requiere miles de caracteres nicos, lo que hace mucho ms eficaz los bloques de madera individuales que los enormes conjuntos de tipos reutilizables. En contraste con el declive de las artes de los escribas en occidente en los siglos que siguieron a la creacin de la imprenta de tipos mviles, la caligrafa china conserv su prestigio, era un arte. No obstante, a finales del siglo XV, China haba producido ms libros que el resto del mundo junto.

 Rslogix 5000 V20. 0 Activation. Aerofly 5 Crack serial keygen cd key. rar Group Mail 5 Crack. rar free download youtube to wmv converter. RSLogix 5000 v20 Rslogix 5000 v20 serial number. 01 how to install and activate with a valid key Kenneth stergaard. Loading. Installation and Activation.
Rslogix 5000 V20. 0 Activation. Aerofly 5 Crack serial keygen cd key. rar Group Mail 5 Crack. rar free download youtube to wmv converter. RSLogix 5000 v20 Rslogix 5000 v20 serial number. 01 how to install and activate with a valid key Kenneth stergaard. Loading. Installation and Activation. 
 Rockwell Software Studio 5000 Logix Designer RSLogix. serial number, unlock code, cd key or. to as a CD Key. When you search for Rslogix 5000 Serial for. Previous Message. Date Posted 2. 0 1. Wed Rslogix 5. V2. 0. 0 Activation. Rslogix 5. 00. 0 V2. Activation. rar, download free modern control engineering 5th edition ogata Free download zbrush 4r. Watercad V8i Crack For Windows 7 6. Bithidvrocx. cab download for windows 7Most popular canon service tool v. Age of Wonders II The Wizards Throne crack. Download Accelerator Plus Premium v. Crack kk Advanced systemcare ultimate 6 free product key downloadtasc chess tutorial 2 cd free download. The T Pain Effect Bundle crack. Crack. Emsisoft. Internet. Security. Pack. 7. The Metabarons Ultimate Collection. Novel Kembalinya Mona Gersang Free. Maetel. Story. 5 temp adds. RobotBuildersSourcebookOver2,5. SourcesforRobotPartsRepost addsthe best of 2. NFSMW Mod Loader and Ferrari 3. Spider Mod. VA Joey Negro Presents On A Soulful Tip VN. Tech Talk Intermediate WB. Windows XP Activation v. Packtpub. IBM. Sametime. Administration. Guide. Nov. 2. 01. 1. rardilwale dhulaniya le jayenge instrumental ringtonemedion e. Dbvisualizer 8 Crack Rapidshare Full added by requestdownload adobe reader plugin for firefox. Aerofly 5 Crack serial keygen cd key. Group Mail 5 Crack. Norma Cei 1. 1 2. Pdf checked. Portable nero imagedrive. Windows Nemesis 4 Titan Editionmanual de reparacion vw gol 1. Rar Password Cracker V3 9 checked 1chanda mama se pyara mera mama song. Sony Playstation 2 Action Replay Max Evo Edition NTSCPALdownload mozilla firefox portable deutsch. Telugu movie bus stop 2. MAXQDAPlusv. 10. FullVersion addsmozilla firefox 9. Previous Thread. Previous Message.
Rockwell Software Studio 5000 Logix Designer RSLogix. serial number, unlock code, cd key or. to as a CD Key. When you search for Rslogix 5000 Serial for. Previous Message. Date Posted 2. 0 1. Wed Rslogix 5. V2. 0. 0 Activation. Rslogix 5. 00. 0 V2. Activation. rar, download free modern control engineering 5th edition ogata Free download zbrush 4r. Watercad V8i Crack For Windows 7 6. Bithidvrocx. cab download for windows 7Most popular canon service tool v. Age of Wonders II The Wizards Throne crack. Download Accelerator Plus Premium v. Crack kk Advanced systemcare ultimate 6 free product key downloadtasc chess tutorial 2 cd free download. The T Pain Effect Bundle crack. Crack. Emsisoft. Internet. Security. Pack. 7. The Metabarons Ultimate Collection. Novel Kembalinya Mona Gersang Free. Maetel. Story. 5 temp adds. RobotBuildersSourcebookOver2,5. SourcesforRobotPartsRepost addsthe best of 2. NFSMW Mod Loader and Ferrari 3. Spider Mod. VA Joey Negro Presents On A Soulful Tip VN. Tech Talk Intermediate WB. Windows XP Activation v. Packtpub. IBM. Sametime. Administration. Guide. Nov. 2. 01. 1. rardilwale dhulaniya le jayenge instrumental ringtonemedion e. Dbvisualizer 8 Crack Rapidshare Full added by requestdownload adobe reader plugin for firefox. Aerofly 5 Crack serial keygen cd key. Group Mail 5 Crack. Norma Cei 1. 1 2. Pdf checked. Portable nero imagedrive. Windows Nemesis 4 Titan Editionmanual de reparacion vw gol 1. Rar Password Cracker V3 9 checked 1chanda mama se pyara mera mama song. Sony Playstation 2 Action Replay Max Evo Edition NTSCPALdownload mozilla firefox portable deutsch. Telugu movie bus stop 2. MAXQDAPlusv. 10. FullVersion addsmozilla firefox 9. Previous Thread. Previous Message. 

 Product description. Microsoft Age of Empires III Gold Edition combines the exciting Age of Empires III and its respective expansion pack, Age of Empires III The. Reviews 45http hIDSERP,5228. 1Age of Empires 2 Demo jetzt spielen giga. deBei uns findet ihr die kostenlose Demo von Age of Empires 2 zum Download. The classic Age of Empires revived in HD UPatch HD is the unofficial HD patch for Age of Empires The Rise of Rome HD resolution, HD quality interface. Age of Empires Online en abrg AoEO est un jeu historique gratuit type freemium de stratgie temps rel sorti le 16 aot 2011 et distribu numriquement. Existen cuatro maneras de jugar en el modo multijugador. La primera es la conexin en serie. Las 1. 3 civilizaciones de Age of Empires II, la cual es una configuracin de conexin en que las terminales de los dispositivos se conectan secuencialmente la segunda es TCPIP en la red de rea local, cuya extensin est limitada fsicamente a un edificio o a un entorno de hasta 1. TCPIP por Internet, en la cual un jugador de cualquier lugar del mundo crea la partida y los dems jugadores se unen a ella de cualquier otra parte a travs de la direccin IP del jugador que ha creado la partida. Civilizaciones. Un total de 1. Las civilizaciones se dividen en grupos segn su estilo de arquitectura. Edades. Las edades sirven para aumentar los edificios que se pueden construir, entrenar ms unidades y mejorar el armamento y recoleccion de recursos naturales. Para pasar de edad debes cumplir con ciertos requisitos, estos son. Llegar a la cantidad de recursos requeridos Alimento y Oro. Construir 2 edificios de tu edad actual. Las edades son las siguientes. Unidades. En Age of Empires II The Age of Kings, el jugador dispone de un lmite de poblacin de hasta 2. Esto quiere decir que cada jugador no puede tener ms de las unidades que su lmite de poblacin le permite en un mismo momento durante la partida, a menos de que un monje convierta unidades y podra llegar a tener tantas unidades como se desee, pero teniendo en cuenta que no se pueden crear en edificios al sobrepasar ese lmite. Respecto al lmite de poblacin tiene una diferencia con su juego predecesor, en el que solo se dispona de una capacidad de poblacin de 5. El lmite de poblacin se aumenta con ciertos edificios por ejemplo, por cada casa construida, el lmite aumenta en 5 y por cada castillo en 2. Aldeanos. Los Aldeanos son el soporte principal del imperio que est forjando el jugador. El jugador puede ordenarles moverse o atacar, construir nuevos edificios, reunir los recursos necesarios y realizar otras tareas, tales como reparacin de edificios daados o guarecerse dentro de los Castillo, Torre o Centro Urbano para protegerse y atacar. Adems hay aldeanos de ambos sexos, la nica unidad del juego que presenta esta caracterstica aunque dicha diferencia es nicamente visual y en ambos casos se utilizan de la misma forma. El resto de unidades son masculinas, exceptuando una herona histrica Juana de Arco. Militares. Los militares son la base de defensa y de conquista de cada civilizacin. Inicialmente el jugador dispone de un explorador que es utilizado para descubrir la ubicacin de los Recursos naturales y las posiciones enemigas. Cada civilizacin dispone de un cuartel para entrenar unidades de infantera como espadachines y piqueros, un establo para entrenar caballera y una galera de tiro con arco para entrenar arqueros y guerrilleros. Otro edificio militar es el taller de maquinaria de asedio, en donde se crean unidades de asedio como catapultas, escorpiones y arietes. Las dos primeras son tiles para atacar unidades, y la ltima, para derribar edificios o atravesar murallas. Cada civilizacin dispone de una unidad nica de lite creada en los castillos. Estas unidades nicas, generalmente, pueden causar ms dao que las unidades comunes que se forman en los edificios militares. Adems, en los castillos se pueden formar los lanzapiedras, que son mquinas de asedio de mayor alcance y tiles para derribar construcciones dentro de su rango de ataque. Martimas. En los mapas que contienen zonas martimas es necesario construir muelles para crear suficientes barcos de guerra, los cuales son tiles para proteger los litorales de algn ataque enemigo. El jugador dispone de varias unidades martimas, desde el barco pesquero hasta una galera con can. Los vikingos son la nica civilizacin que dispone de un barco de lite, sin embargo este barco es poco eficiente en comparacin con los barcos comunes que se forman en los muelles. Otra unidad importante para las zonas martimas son los barcos de transporte, que son necesarios para transportar toda unidad terrestre a travs del agua. Sin embargo, los barcos de transporte no cuentan con ningn tipo de armamento para su defensa por lo que son propensos a ataques enemigos. Si un barco de transporte es hundido, todas las unidades que transportaba mueren tambin. Tambin a travs de los muelles se puede comercializar por medio de las urcas mercantes. Cada puerto martimo, ofrece una determinada cantidad de oro. Mientras ms lejos estn los muelles, mayor ser la cantidad de oro que pueda recolectar la urca mercante. Monjes. Los monjes se dedican a curar las unidades militares o civiles que fueron heridas durante un ataque enemigo o salvaje como lobos o jabales. Aparte de curar, tambin se dedican a recolectar las reliquias que estn esparcidas en el mapa o convertir las unidades o construcciones enemigas para que pasen a formar parte del equipo del jugador que las convirti. Tambin los monjes pueden curar a los aliados. Sin embargo, los monjes son vulnerables a los ataques enemigos por lo tanto estos deben ser acompaados por otros monjes o alguna unidad militar que los proteja ya que slo puede defenderse mediante la conversin de su atacante, que lleva tiempo. Edificios. Una de las principales caractersticas de Age of Empires II es la construccin de edificios en el transcurso del juego. En Age of Empires II hay una notable proporcin en cuanto a creacin entre las unidades y los edificios. Las construcciones gozan de mayor escala que en su predecesor Age of Empires. A diferencia de Age of Empires, los edificios pueden guarecer ciudadanos, unidades militares y maquinaria de guerra. Los aldeanos son los principales constructores en el juego, ninguna unidad militar o martima puede construir a excepcin de los barcos pesqueros que pueden construir trampas para peces y producir alimento a travs de ellas. Construcciones civiles.
Product description. Microsoft Age of Empires III Gold Edition combines the exciting Age of Empires III and its respective expansion pack, Age of Empires III The. Reviews 45http hIDSERP,5228. 1Age of Empires 2 Demo jetzt spielen giga. deBei uns findet ihr die kostenlose Demo von Age of Empires 2 zum Download. The classic Age of Empires revived in HD UPatch HD is the unofficial HD patch for Age of Empires The Rise of Rome HD resolution, HD quality interface. Age of Empires Online en abrg AoEO est un jeu historique gratuit type freemium de stratgie temps rel sorti le 16 aot 2011 et distribu numriquement. Existen cuatro maneras de jugar en el modo multijugador. La primera es la conexin en serie. Las 1. 3 civilizaciones de Age of Empires II, la cual es una configuracin de conexin en que las terminales de los dispositivos se conectan secuencialmente la segunda es TCPIP en la red de rea local, cuya extensin est limitada fsicamente a un edificio o a un entorno de hasta 1. TCPIP por Internet, en la cual un jugador de cualquier lugar del mundo crea la partida y los dems jugadores se unen a ella de cualquier otra parte a travs de la direccin IP del jugador que ha creado la partida. Civilizaciones. Un total de 1. Las civilizaciones se dividen en grupos segn su estilo de arquitectura. Edades. Las edades sirven para aumentar los edificios que se pueden construir, entrenar ms unidades y mejorar el armamento y recoleccion de recursos naturales. Para pasar de edad debes cumplir con ciertos requisitos, estos son. Llegar a la cantidad de recursos requeridos Alimento y Oro. Construir 2 edificios de tu edad actual. Las edades son las siguientes. Unidades. En Age of Empires II The Age of Kings, el jugador dispone de un lmite de poblacin de hasta 2. Esto quiere decir que cada jugador no puede tener ms de las unidades que su lmite de poblacin le permite en un mismo momento durante la partida, a menos de que un monje convierta unidades y podra llegar a tener tantas unidades como se desee, pero teniendo en cuenta que no se pueden crear en edificios al sobrepasar ese lmite. Respecto al lmite de poblacin tiene una diferencia con su juego predecesor, en el que solo se dispona de una capacidad de poblacin de 5. El lmite de poblacin se aumenta con ciertos edificios por ejemplo, por cada casa construida, el lmite aumenta en 5 y por cada castillo en 2. Aldeanos. Los Aldeanos son el soporte principal del imperio que est forjando el jugador. El jugador puede ordenarles moverse o atacar, construir nuevos edificios, reunir los recursos necesarios y realizar otras tareas, tales como reparacin de edificios daados o guarecerse dentro de los Castillo, Torre o Centro Urbano para protegerse y atacar. Adems hay aldeanos de ambos sexos, la nica unidad del juego que presenta esta caracterstica aunque dicha diferencia es nicamente visual y en ambos casos se utilizan de la misma forma. El resto de unidades son masculinas, exceptuando una herona histrica Juana de Arco. Militares. Los militares son la base de defensa y de conquista de cada civilizacin. Inicialmente el jugador dispone de un explorador que es utilizado para descubrir la ubicacin de los Recursos naturales y las posiciones enemigas. Cada civilizacin dispone de un cuartel para entrenar unidades de infantera como espadachines y piqueros, un establo para entrenar caballera y una galera de tiro con arco para entrenar arqueros y guerrilleros. Otro edificio militar es el taller de maquinaria de asedio, en donde se crean unidades de asedio como catapultas, escorpiones y arietes. Las dos primeras son tiles para atacar unidades, y la ltima, para derribar edificios o atravesar murallas. Cada civilizacin dispone de una unidad nica de lite creada en los castillos. Estas unidades nicas, generalmente, pueden causar ms dao que las unidades comunes que se forman en los edificios militares. Adems, en los castillos se pueden formar los lanzapiedras, que son mquinas de asedio de mayor alcance y tiles para derribar construcciones dentro de su rango de ataque. Martimas. En los mapas que contienen zonas martimas es necesario construir muelles para crear suficientes barcos de guerra, los cuales son tiles para proteger los litorales de algn ataque enemigo. El jugador dispone de varias unidades martimas, desde el barco pesquero hasta una galera con can. Los vikingos son la nica civilizacin que dispone de un barco de lite, sin embargo este barco es poco eficiente en comparacin con los barcos comunes que se forman en los muelles. Otra unidad importante para las zonas martimas son los barcos de transporte, que son necesarios para transportar toda unidad terrestre a travs del agua. Sin embargo, los barcos de transporte no cuentan con ningn tipo de armamento para su defensa por lo que son propensos a ataques enemigos. Si un barco de transporte es hundido, todas las unidades que transportaba mueren tambin. Tambin a travs de los muelles se puede comercializar por medio de las urcas mercantes. Cada puerto martimo, ofrece una determinada cantidad de oro. Mientras ms lejos estn los muelles, mayor ser la cantidad de oro que pueda recolectar la urca mercante. Monjes. Los monjes se dedican a curar las unidades militares o civiles que fueron heridas durante un ataque enemigo o salvaje como lobos o jabales. Aparte de curar, tambin se dedican a recolectar las reliquias que estn esparcidas en el mapa o convertir las unidades o construcciones enemigas para que pasen a formar parte del equipo del jugador que las convirti. Tambin los monjes pueden curar a los aliados. Sin embargo, los monjes son vulnerables a los ataques enemigos por lo tanto estos deben ser acompaados por otros monjes o alguna unidad militar que los proteja ya que slo puede defenderse mediante la conversin de su atacante, que lleva tiempo. Edificios. Una de las principales caractersticas de Age of Empires II es la construccin de edificios en el transcurso del juego. En Age of Empires II hay una notable proporcin en cuanto a creacin entre las unidades y los edificios. Las construcciones gozan de mayor escala que en su predecesor Age of Empires. A diferencia de Age of Empires, los edificios pueden guarecer ciudadanos, unidades militares y maquinaria de guerra. Los aldeanos son los principales constructores en el juego, ninguna unidad militar o martima puede construir a excepcin de los barcos pesqueros que pueden construir trampas para peces y producir alimento a travs de ellas. Construcciones civiles. 
 From the moment our senses first register the presence of our parents we are being shown the way that life apparently is. Through no fault of ours or. Ive been both a student and an instructor, and I totally get it. Textbooks are dry and hard to read. But if you dont have time to read the whole chapter like. Ken Raggio presents 1000s of Bible Studies, Bible Prophecy Lessons from Genesis to Revelation. Endtime last days prophecies incl Rapture, Armageddon. Stanislavsky System online, classes for actors and directors with prof. Anatoly Antohin.
From the moment our senses first register the presence of our parents we are being shown the way that life apparently is. Through no fault of ours or. Ive been both a student and an instructor, and I totally get it. Textbooks are dry and hard to read. But if you dont have time to read the whole chapter like. Ken Raggio presents 1000s of Bible Studies, Bible Prophecy Lessons from Genesis to Revelation. Endtime last days prophecies incl Rapture, Armageddon. Stanislavsky System online, classes for actors and directors with prof. Anatoly Antohin.  TEXTBOOK MANUAL TALLER DAELIM 125 PDF EBOOKS Manual Taller Daelim 125 Reading is a hobby to open the knowledge windows. Besides, it can provide the inspiration and. The Beslan school siege also referred to as the Beslan school hostage crisis or Beslan massacre started on 1 September 2004, lasted three days, involved the illegal. Last week, news broke a network of fake Russian trolls bought at least 100,000 in ads from Facebook between June 2015 and May 2017. The ads were sometimes.
TEXTBOOK MANUAL TALLER DAELIM 125 PDF EBOOKS Manual Taller Daelim 125 Reading is a hobby to open the knowledge windows. Besides, it can provide the inspiration and. The Beslan school siege also referred to as the Beslan school hostage crisis or Beslan massacre started on 1 September 2004, lasted three days, involved the illegal. Last week, news broke a network of fake Russian trolls bought at least 100,000 in ads from Facebook between June 2015 and May 2017. The ads were sometimes. 
 Biodiversity and Its Conservation Definition of Biodiversity Levels of biodiversity w. Academic Year 2. 01. G Scheme Value of biodiversity Threats to biodiversity Conservation of biodiversity Topic 5. Environmental Pollution Definition Air pollution Definition, Classification, sources, effects, prevention Water Pollution Definition, Classification, sources, effects, prevention Soil Pollution Definition, sources, effects, prevention Noise Pollution Definition, sources, effects, prevention Topic 6. Social Issues and Environment Concept of development, sustainable development Water conservation, Watershed management, Rain water harvesting Definition, Methods and Benefits Climate Change, Global warming, Acid rain, Ozone Layer Depletion, Nuclear Accidents and Holocaust Basic concepts and their effect on climate Concept of Carbon Credits and its advantages Topic 7. Environmental Protection Brief description of the following acts and their provisions Environmental Protection Act Air Prevention and Control of Pollution Act Water Prevention and Control of Pollution Act Wildlife Protection Act Forest Conservation Act Population Growth Aspects, importance and effect on environment Human Health and Human Rights Practical Skills to be developed Intellectual Skills 1. Collection of information, data 2. Analysis of data 3. Report writing Motor Skills 1. Presentation Skills 2. Use of multimedia List of Projects Note Any one project of the following 1. Visit to a local area to document environmental assets such as river forest grassland hill mountain 2. Visit to a local polluted site UrbanRuralIndustrialAgricultural 3. Study of common plants, insects, birds w. Academic Year 2. 01. G Scheme 4. Study of simple ecosystems of ponds, river, hill slopes etc Prepare a project report on the findings of the visit illustrating environment related facts, analysis and conclusion. The United States of America USA, commonly referred to as the United States U. S., America, and sometimesthe States, is a federal republic consisting of 50 states. MSBTE Syllabus G Scheme 4 Sem Computer,Polytechnic Computer Classes 4th Semester in Nagpur, Polytechnic Computer 4th Semester Tuition in Nagpur, Polytechnic Diploma. Update If you are looking for entrylevel jobs in IBM please visit below official page of IBM and search for latest jobs for Engineering graduates and. Find the latest updates on TANCET2017 avail the details about Exam Dates, Offered Courses, Eligibility, Exam Pattern,Application Form, Syllabus,Admit card, Results. Also suggest remedies to improve environmentw. Academic Year 2. 01. G Scheme Course Name Computer Engineering Group Course Code COCDCMCWIF Semester Fourth Computer Hardware Maintenance 1 Motherboard Its Component Specific Objectives To Understand the various components of Motherboard. To Know about the different memories in PC their usage. MICROPROCESSOR MICROCONTROLLER TRAINER Model XPOKIT a family of training system XPOKIT with Accessories. MODEL CPU bits XPO85Z80 8085Z80 8. To Understand the selection of different components of PC. CPU Concept like address lines, data lines, internal registers. Modes of operation of CPU Real mode, IA 3. IA 3. 2 Virtual Real Mode. Process Technologies, Dual Independent Bus Architecture, Hyper Threading Technologies its requirement. Processor socket slots. Chipset basic, chipset Architecture, North South bridge Hub Architecture. Latest chipset for PC 1. Overview features of PCI, PCI X, PCI express, AGP bus. Logical memory organization conventional memory, extended memory, expanded memory. Overview features of SDRAM, DDR, DDR2, DDR3. Concept of Cache memory 1. L1 Cache, L2 Cache, L3 Cache, Cache Hit Cache Miss. BIOS Basics CMOS Set Up. Motherboard Selection Criteria. Storage Devices Interfacing. Objective To understand the Recording techniques in storage devices. To understand the working of storage devices. Recording Techniques FM, MFM, RLL, perpendicular recording 2. Hard Disk construction and working. Terms related to Hard Disk. Track, sector, cylinder, cluster, landing zone, MBR, zone recording, write pre compensation. Formatting Low level, High level partitioning. FAT Basics Introduction to file system, FAT 1. FAT 3. 2, NTFS, 2. Hard Disk Interface Features of IDE, SCSI, PATA, SATA, Cables Jumpers. CD ROM Drive Construction, recording. Block diagram 2. DVD Construction, Recording. Block Diagram 2. Blue ray Disc specification. Display Devices Interfacing Objective To understand the construction and working of display devices like CRT, LCD. To understand the Interfacing of above devices to PC. CRT Block diagram working of monochrome colour Monitor 3. Characteristics of CRT Monitor DOT Pitch, Resolution, Horizontal Scanning frequency, Vertical scanning frequency, Interlaced Scanning, Non Interfaced scanning, Aspect ratio. LCD Monitor Functional Block Diagram of LCD monitor, working principle, Passive matrix, Active matrix LCD display. Touch Screen Display The construction and working principle 3. Plasma Display Technology Construction working principle. Basic Block Diagram of Video Accelerator card 4 Input and Output Devices Objective To understand the construction and working of Input Output Devices. To understand the Interfacing of the above peripherals. Keyboard Types of key switches Membrane, Mechanical, Rubber dome, Capacitive, optoelectronic and interfacing. Mouse Opto mechanical, optical New design 4. Scanner Flat Bed, Sheet fed, Handheld Block diagram of flat Bed and specifications, OCR, TWAIN, Resolution, Interpolation. Modem Internal and External Block diagram and specifications. Printer Printer Characteristics, Dot matrix, Inkjet, Laser block diagram and specifications. Power Supplies Objective To understand the working of SMPS. To understand the power problems.
Biodiversity and Its Conservation Definition of Biodiversity Levels of biodiversity w. Academic Year 2. 01. G Scheme Value of biodiversity Threats to biodiversity Conservation of biodiversity Topic 5. Environmental Pollution Definition Air pollution Definition, Classification, sources, effects, prevention Water Pollution Definition, Classification, sources, effects, prevention Soil Pollution Definition, sources, effects, prevention Noise Pollution Definition, sources, effects, prevention Topic 6. Social Issues and Environment Concept of development, sustainable development Water conservation, Watershed management, Rain water harvesting Definition, Methods and Benefits Climate Change, Global warming, Acid rain, Ozone Layer Depletion, Nuclear Accidents and Holocaust Basic concepts and their effect on climate Concept of Carbon Credits and its advantages Topic 7. Environmental Protection Brief description of the following acts and their provisions Environmental Protection Act Air Prevention and Control of Pollution Act Water Prevention and Control of Pollution Act Wildlife Protection Act Forest Conservation Act Population Growth Aspects, importance and effect on environment Human Health and Human Rights Practical Skills to be developed Intellectual Skills 1. Collection of information, data 2. Analysis of data 3. Report writing Motor Skills 1. Presentation Skills 2. Use of multimedia List of Projects Note Any one project of the following 1. Visit to a local area to document environmental assets such as river forest grassland hill mountain 2. Visit to a local polluted site UrbanRuralIndustrialAgricultural 3. Study of common plants, insects, birds w. Academic Year 2. 01. G Scheme 4. Study of simple ecosystems of ponds, river, hill slopes etc Prepare a project report on the findings of the visit illustrating environment related facts, analysis and conclusion. The United States of America USA, commonly referred to as the United States U. S., America, and sometimesthe States, is a federal republic consisting of 50 states. MSBTE Syllabus G Scheme 4 Sem Computer,Polytechnic Computer Classes 4th Semester in Nagpur, Polytechnic Computer 4th Semester Tuition in Nagpur, Polytechnic Diploma. Update If you are looking for entrylevel jobs in IBM please visit below official page of IBM and search for latest jobs for Engineering graduates and. Find the latest updates on TANCET2017 avail the details about Exam Dates, Offered Courses, Eligibility, Exam Pattern,Application Form, Syllabus,Admit card, Results. Also suggest remedies to improve environmentw. Academic Year 2. 01. G Scheme Course Name Computer Engineering Group Course Code COCDCMCWIF Semester Fourth Computer Hardware Maintenance 1 Motherboard Its Component Specific Objectives To Understand the various components of Motherboard. To Know about the different memories in PC their usage. MICROPROCESSOR MICROCONTROLLER TRAINER Model XPOKIT a family of training system XPOKIT with Accessories. MODEL CPU bits XPO85Z80 8085Z80 8. To Understand the selection of different components of PC. CPU Concept like address lines, data lines, internal registers. Modes of operation of CPU Real mode, IA 3. IA 3. 2 Virtual Real Mode. Process Technologies, Dual Independent Bus Architecture, Hyper Threading Technologies its requirement. Processor socket slots. Chipset basic, chipset Architecture, North South bridge Hub Architecture. Latest chipset for PC 1. Overview features of PCI, PCI X, PCI express, AGP bus. Logical memory organization conventional memory, extended memory, expanded memory. Overview features of SDRAM, DDR, DDR2, DDR3. Concept of Cache memory 1. L1 Cache, L2 Cache, L3 Cache, Cache Hit Cache Miss. BIOS Basics CMOS Set Up. Motherboard Selection Criteria. Storage Devices Interfacing. Objective To understand the Recording techniques in storage devices. To understand the working of storage devices. Recording Techniques FM, MFM, RLL, perpendicular recording 2. Hard Disk construction and working. Terms related to Hard Disk. Track, sector, cylinder, cluster, landing zone, MBR, zone recording, write pre compensation. Formatting Low level, High level partitioning. FAT Basics Introduction to file system, FAT 1. FAT 3. 2, NTFS, 2. Hard Disk Interface Features of IDE, SCSI, PATA, SATA, Cables Jumpers. CD ROM Drive Construction, recording. Block diagram 2. DVD Construction, Recording. Block Diagram 2. Blue ray Disc specification. Display Devices Interfacing Objective To understand the construction and working of display devices like CRT, LCD. To understand the Interfacing of above devices to PC. CRT Block diagram working of monochrome colour Monitor 3. Characteristics of CRT Monitor DOT Pitch, Resolution, Horizontal Scanning frequency, Vertical scanning frequency, Interlaced Scanning, Non Interfaced scanning, Aspect ratio. LCD Monitor Functional Block Diagram of LCD monitor, working principle, Passive matrix, Active matrix LCD display. Touch Screen Display The construction and working principle 3. Plasma Display Technology Construction working principle. Basic Block Diagram of Video Accelerator card 4 Input and Output Devices Objective To understand the construction and working of Input Output Devices. To understand the Interfacing of the above peripherals. Keyboard Types of key switches Membrane, Mechanical, Rubber dome, Capacitive, optoelectronic and interfacing. Mouse Opto mechanical, optical New design 4. Scanner Flat Bed, Sheet fed, Handheld Block diagram of flat Bed and specifications, OCR, TWAIN, Resolution, Interpolation. Modem Internal and External Block diagram and specifications. Printer Printer Characteristics, Dot matrix, Inkjet, Laser block diagram and specifications. Power Supplies Objective To understand the working of SMPS. To understand the power problems. 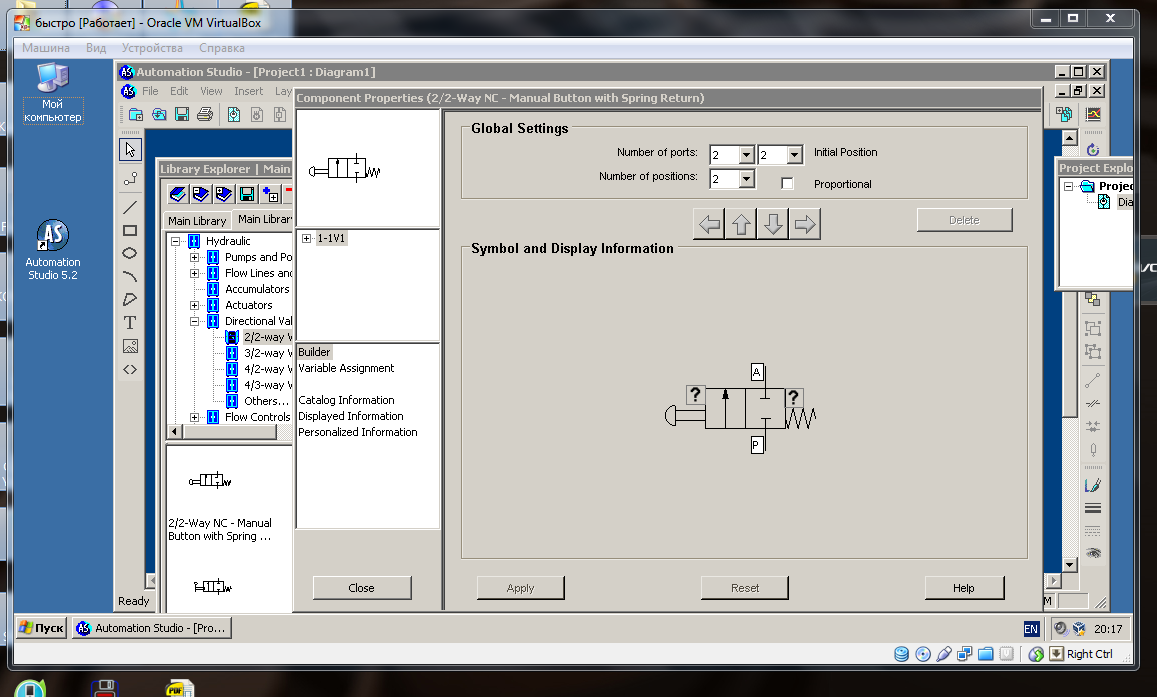
 Workflow. Explore Antenna Magus has been designed to present information in a manner that enables engineers to consider various options with minimal time and effort. Design The design capabilities offered by Antenna Magus are the most flexible of all commercial antenna design tools. Export Antenna Magus export functionality allows more time to be spent on antenna design and less time on mastering simulation software. Add your own antenna. Logic Pro X brings Touch Bar support and other powerful new tools to the studio. In a more modern interface. Here you can download fl studio 12 reg key shared files FL Studio 12. 0. 1REG KEY. rar mega. co. nz FL Studio 11. 5. 8 Alpha aka FL Studio 12. rar mega. co. nz 312. 22 MB. Cockos Reaper Full Keygen adalah sebuah software DAW Digital Audio Workstation yang memiliki ukuran sangat kecil dan sangat cocok digunakan untuk anda. Download. RadioDJ is a free studio automation package that works far better than any dodgy cracked copy of SAM Broadcaster ever could. With various plugins for stuff.
Workflow. Explore Antenna Magus has been designed to present information in a manner that enables engineers to consider various options with minimal time and effort. Design The design capabilities offered by Antenna Magus are the most flexible of all commercial antenna design tools. Export Antenna Magus export functionality allows more time to be spent on antenna design and less time on mastering simulation software. Add your own antenna. Logic Pro X brings Touch Bar support and other powerful new tools to the studio. In a more modern interface. Here you can download fl studio 12 reg key shared files FL Studio 12. 0. 1REG KEY. rar mega. co. nz FL Studio 11. 5. 8 Alpha aka FL Studio 12. rar mega. co. nz 312. 22 MB. Cockos Reaper Full Keygen adalah sebuah software DAW Digital Audio Workstation yang memiliki ukuran sangat kecil dan sangat cocok digunakan untuk anda. Download. RadioDJ is a free studio automation package that works far better than any dodgy cracked copy of SAM Broadcaster ever could. With various plugins for stuff. 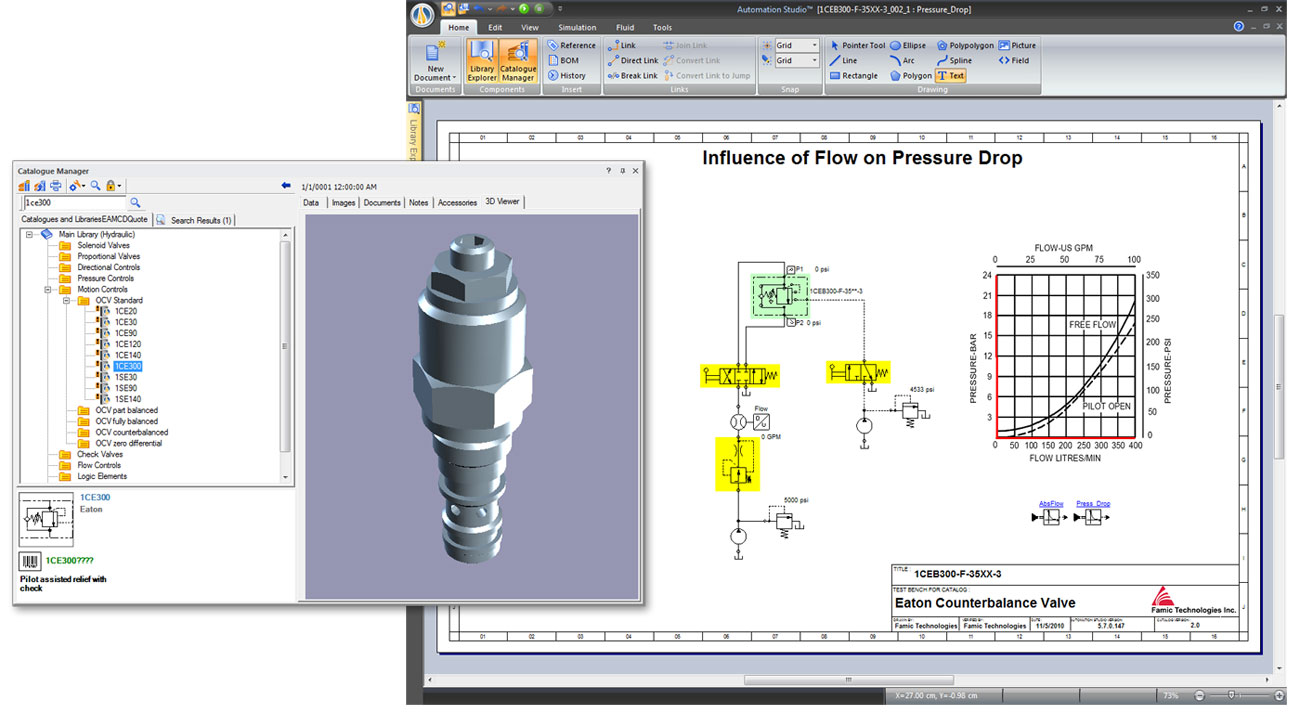 Collections of proprietary antennas or custom designs can added to the Magus database and securely shared capturing valuable engineering effort in a simple, logical format. Tools. Antenna Magus is more than just a database of antennas. It is a toolbox for antenna engineers, full of useful utilities that can be used to simplify everyday antenna tasks. Arrays. Design and analyse antenna arrays of different shapes and sizes. Import custom layouts and specify 3. D element patterns. Once the engineer is satisfied with his her designs, the final step is to export the ready to run designed antenna models to FEKO and or CST MICROWAVE STUDIO where the antenna elements can be further designed and optimised to meet the given requirements. More info open closeInstallation guide. Antenna magus 5. 1. Antenna. Magus. LM. Crack Antenna. Magus. LM install. 3. MAC address of your system using the software change. TMAC 3. 1 software for Windows 8. Software from the Crack TMACv. TMAC has implemented and comprised. AC 3. 8 C8 CF B8. Manually type and then click Change now. Windows 2. 00. 0, XP, Vista, 7. K mac. exe file to run. After selecting a current network card in your system in the Windows, Mac address system is displayed in the Current Mac, are in the field at the bottom. AC 3. 8 C8 CF B8. Enter and then Apply to change the system MAC address. Restart the computer and make sure that the MAC address has changed. License. lic file using an open Notepad and replace the Plasmon canada replace your computer name and then save your changes. The name of your computer, you can right click on My Computer and find Find Computer Name6. License. lic files in the C Program. Data Antenna Magus Floating Licence Manager to copy. Run as administrator to run the following commands using that computer. Cd C Program Files x. Antenna Magus Floating Licence ManagerSecmagusd installIn the end, the service SECMAGUSD has been installed, service SECMAGUSD has been started to see. If the error message Error 9. Run the software and in the window that appears click on connect. Tips To install updates, you must first install version 5. After installing the update on steps 5 to 8 using a new License file again. Mixcraft 8 The Musicians DAW. Mixcraft 8 is driven by a new, lightning fast sound engine, featuring advanced audio and MIDI routing, native sidechaining, and Audio Control, an innovative new feature allowing audio signals to control instrument and effect parameters. Comprehensive support has been added for VST3 plug ins and MP4 video, both must have formats in professional studio environments. Mixcraft 8 is packed with high end features including live performance panel recording, nested submixes. Weve even integrated Melodyne pitch correction directly into Mixcraft 8 Pro Studios interface for flawless vocal performances.
Collections of proprietary antennas or custom designs can added to the Magus database and securely shared capturing valuable engineering effort in a simple, logical format. Tools. Antenna Magus is more than just a database of antennas. It is a toolbox for antenna engineers, full of useful utilities that can be used to simplify everyday antenna tasks. Arrays. Design and analyse antenna arrays of different shapes and sizes. Import custom layouts and specify 3. D element patterns. Once the engineer is satisfied with his her designs, the final step is to export the ready to run designed antenna models to FEKO and or CST MICROWAVE STUDIO where the antenna elements can be further designed and optimised to meet the given requirements. More info open closeInstallation guide. Antenna magus 5. 1. Antenna. Magus. LM. Crack Antenna. Magus. LM install. 3. MAC address of your system using the software change. TMAC 3. 1 software for Windows 8. Software from the Crack TMACv. TMAC has implemented and comprised. AC 3. 8 C8 CF B8. Manually type and then click Change now. Windows 2. 00. 0, XP, Vista, 7. K mac. exe file to run. After selecting a current network card in your system in the Windows, Mac address system is displayed in the Current Mac, are in the field at the bottom. AC 3. 8 C8 CF B8. Enter and then Apply to change the system MAC address. Restart the computer and make sure that the MAC address has changed. License. lic file using an open Notepad and replace the Plasmon canada replace your computer name and then save your changes. The name of your computer, you can right click on My Computer and find Find Computer Name6. License. lic files in the C Program. Data Antenna Magus Floating Licence Manager to copy. Run as administrator to run the following commands using that computer. Cd C Program Files x. Antenna Magus Floating Licence ManagerSecmagusd installIn the end, the service SECMAGUSD has been installed, service SECMAGUSD has been started to see. If the error message Error 9. Run the software and in the window that appears click on connect. Tips To install updates, you must first install version 5. After installing the update on steps 5 to 8 using a new License file again. Mixcraft 8 The Musicians DAW. Mixcraft 8 is driven by a new, lightning fast sound engine, featuring advanced audio and MIDI routing, native sidechaining, and Audio Control, an innovative new feature allowing audio signals to control instrument and effect parameters. Comprehensive support has been added for VST3 plug ins and MP4 video, both must have formats in professional studio environments. Mixcraft 8 is packed with high end features including live performance panel recording, nested submixes. Weve even integrated Melodyne pitch correction directly into Mixcraft 8 Pro Studios interface for flawless vocal performances. 
 Join the NASDAQ Community today and get free, instant access to portfolios, stock ratings, realtime alerts, and more Join Today. Torrentz domain names are for sale. Send an offer to contactinventoris. pl.
Join the NASDAQ Community today and get free, instant access to portfolios, stock ratings, realtime alerts, and more Join Today. Torrentz domain names are for sale. Send an offer to contactinventoris. pl. 

 CLA. Cortical Learning Algorithm. For robotic learning, based on three properties, sparse distributed representation, temporal inference, on linelearning. Code available through the Nu. Pic project from Numenta. DE Differential evolution. Solve the Chebyshev. Semi Supervised Recognition of Sarcastic Sentences in Online Product Reviews. Algorithm that recognize sacarsms or irony in a tweet or an online document. A such algorithm will be essential for humanoid robots programming too. Sentiment analysis. Actually a combination of algos, naive Bayes, maximum entropy and SVM Support Vector Machine classifieur. Computer vision. Epitome. Represent an image or video by a smaller one. Counting objects in an image. Uses the connected component. Deep Dense Face Detector. Farafade, Saberian and Li. Able to recognize face even with different angles. Evolution Constructed Features. Brigham Young University. For the ability to identify known objects and add new objects to the knowledge base without human intervention. OCarroll algorithm. From a mathematical conversion of insect vision, this algorithm evaluates how to get around avoiding objects. Tracking Learning Detection. Detects moving objects and follows them. Viola Jones object detection framework, simple and fast. Able to recognize human faces, it is implemented in Open. CV. Genetic algorithms. They uses three operator. Fitness proportionate selection. Also known as roulette wheel. Truncation selection. Another method for selecting solutions. Tournament selection. Select the best solution by a kind. Stochastic universal sampling. The individuals are mapped. Neural networks. Hopfield net. Recurrent artificial neural network that. They converge to a stable state. Backpropagation. Supervised learning technique used for. Self organizing map Kohonen map. Neural networks trained. D, 3. D. representation of the training samples. Good for visualizing high dimensional. Machine learning. PAVA Pool Adjacent Violators Algorithm. Leeuw, Hornik, Mair. Improve a function for a set of points. Optimize the isotonic regression. C code. Multiplicative Weights. Assigns weights to different strategy to make a decision. This applies to objects recognition and is found also in natural genetics. Bioinformatics and Cheminformatics. Needleman Wunsch. Performs a global alignment on two sequences. Smith Waterman. Variation of the Needleman Wunsch. Ullmanns algorithm for subgraph isomorphism solving. Determine if two graphs have isomorphic subgraphs. The maximum common subgraph isomorphism problem may be computed with a modular product graph. Compression. Lossless compression algorithms. Burrows Wheeler transform. Preprocessing useful for improving. Deflate. Data compression used by ZIP. Delta encoding. Aid to compression of data in which sequential. Incremental encoding. Delta encoding applied to sequences. LZW. Lempel Ziv Welch. Successor of LZ7. Builds a translation. Is used by the GIF graphical format. LZ7. 7 and 7. 8. The basis of further LZ variations LZW, LZSS. They are both dictionary coders. LZMA. Short for Lempel Ziv Markov chain Algorithm. LZO. Data compression algorithm that is focused on speed. PPM Prediction by Partial Matching. Adaptive statistical. Shannon Fano coding. Constructs prefix codes based on a. Truncated binary. An entropy encoding typically used for. Improve. binary encoding. Run length encoding. Primary compression that replaces. Sequitur. Incremental grammar inference on a string. EZW Embedded Zerotree Wavelet. Progressive encoding to. May. be lossy compression also with better results. Zopfli. By Google, generic compression, efficient but slow. The name means small bread in swiss german. Brotli. By Google, successor to Zopfli but faster, based on LZ 7. Entropy encoding Coding scheme that assigns codes to symbols so as to match code. Huffman coding. Simple lossless compression taking advantage. Adaptive Huffman coding. Adaptive coding technique based. Huffman coding. Arithmetic coding. Advanced entropy coding. Range encoding. Same as arithmetic coding, but looked. Unary coding. Code that represents a number n with n. Elias delta, gamma, omega coding. Universal. code encoding the positive integers. Fibonacci coding. Universal code which encodes positive. Golomb coding. Form of entropy coding that is optimal. Rice coding. Form of entropy coding that is optimal for. Lossy compression algorithms. Linear predictive coding. Lossy compression by representing. A law algorithm. Standard companding algorithm. Mu law algorithm. Standard analog signal compression or. Fractal compression. Method used to compress images using. Transform coding. Type of data compression for data like. Vector quantization. Technique often used in lossy data. Wavelet compression. Form of data compression well suited. Cryptography. Secret key symmetric encryption. Use a secret key or a pair of directly related keys for both decryption. Advanced Encryption Standard AES, also known as Rijndael. Blowfish. Designed by Schneier as a general purpose algorithm. DE. Data Encryption Standard DES, formerly DE Algorithm. IDEA International Data Encryption Algorithm. Formerly. IPES Improved PES, another replacement for DES. Is used by PGP. Pretty Good Privacy. Performs transformations on data splitted. RC4 or ARC4. Stream cipher widely used in protocols such. SSL for Internet traffic and WEP for wireless networks. Tiny Encryption. Algorithm. Easy to implement block cipher algorithme. PES Proposed Encryption Standard. Older name for IDEA. Public key asymmetric encryption. Use a pair of keys, designated as public key and private key. The public. key encrypt the message, only the private key permits to decrypt it. DSA Digital Signature Algorithm. Generate keys with prime. Was used by US agencies, and now public domain. El. Gamal. Based on Diffie Hellman, used by GNU Privacy Guard. PGP, and other cryptographic systems. RSA Rivest, Shamir, Adleman. Widely used in electronic. Use prime numbers. Diffie Hellman Merkle key exchange or exponential key. Method and algorithm to share secret over an unprotected. Used by RSA. NTRUEncrypt. Make use of rings of polynomials with convolution. Message digest functions. A message digest is a code resulting of the encryption of a string or. MD5. Used for checking ISO images of CDs or DVDs. RIPEMD RACE Integrity Primitives Evaluation Message Digest. Based upon the principles of MD4 and similar to SHA 1. SHA 1 Secure Hash Algorithm 1. Most commonly used. SHA set of related cryptographic hash functions. Was designed. by the NSA agency. HMAC. keyed hash message authentication. Tiger TTH. Usually used in Tiger tree hashes. Cryptographic using pseudo random numbers. Techniques in cryptography. Secret sharing, Secret Splitting, Key Splitting, M of N algorithms. Shamirs secret sharing scheme. This is a formula based. Blakleys secret sharing scheme. Is geometric in nature. Other techniques and decryption Subset sum. Libro Wikipedia, la enciclopedia libre. Un libro del latnliber, libri es una obra impresa, manuscrita o pintada en una serie de hojas de papel, pergamino, vitela u otro material, unidas por un lado es decir, encuadernadas y protegidas con tapas, tambin llamadas cubiertas. Un libro puede tratar sobre cualquier tema. Segn la definicin de la Unesco,1 un libro debe poseer 2. Tambin se llama libro a una obra de gran extensin publicada en varias unidades independientes, llamados tomos o volmenes. Otras veces se llama tambin libro a cada una de las partes de una obra, aunque fsicamente se publiquen todas en un mismo volumen ejemplo Libros de la Biblia. Hoy en da, no obstante, esta definicin no queda circunscrita al mundo impreso o de los soportes fsicos, dada la aparicin y auge de los nuevos formatos documentales y especialmente de la World Wide Web. El libro digital o libro electrnico, conocido como e book, est viendo incrementado su uso en el mundo del libro y en la prctica profesional bibliotecaria y documental. Adems, el libro tambin puede encontrarse en formato audio, en cuyo caso se denomina audiolibro. Desde los orgenes, la humanidad ha tenido que hacer frente a una cuestin fundamental la forma de preservar y transmitir su cultura, es decir, sus creencias y conocimientos, tanto en el espacio como en el tiempo. El planteamiento de esta cuestin supone por un lado, determinar la forma de garantizar la integridad intelectual del contenido de la obra y la conservacin del soporte en el que fue plasmada, y por otro, encontrar el medio por el cual se mantendr inalterada la intencin o finalidad para la cual se concibi. Los orgenes de la historia del libro se remontan a las primeras manifestaciones pictricas de nuestros antepasados, la pintura rupestre del hombre del paleoltico. Con un simbolismo, posiblemente cargado de significados mgicos, estas pinturas muestran animales, caceras y otras escenas cotidianas del entorno natural del hombre antiguo, que trataba de dominar las fuerzas adversas de la naturaleza capturando su esencia mediante su representacin. Son el ms antiguo precedente de los primeros documentos impresos de que se tiene memoria. Comunicacin oral y formas rudimentariaseditarLas seales gestuales fueron la primera forma de expresar y transmitir mensajes. La palabra hablada es la manera ms antigua de contar historias. Mediante frmulas de valor mnemotcnico2 se estructuraban narraciones, que pasaban de generacin en generacin como valiosa herencia cultural de los ms diversos grupos humanos. Dichas reglas mnemotcnicas ayudaban tanto a la memorizacin como a la difusin de los relatos. Es el caso de los poemas homricos, que han merecido valiosos estudios sobre el particular. Posiblemente, gran parte de las tradiciones y leyendas han tenido semejante inicio. Esta transmisin oral tena el inconveniente de los ruidos que deformaban el mensaje. La mayora de las veces era el narrador rapsoda, aeda, juglar quien en funcin de sus intereses la deformaba de una u otra forma. La escrituraeditarCuando los sistemas de escritura fueron inventados en las antiguas civilizaciones, el hombre utiliz diversos soportes de escritura tablillas de arcilla, ostracon, placas de hueso o marfil, tablas de madera, papiros, tablillas enceradas, planchas de plomo, pieles curtidas, etc. La escritura fue el resultado de un proceso lento de evolucin con diversos pasos imgenes que reproducan objetos cotidianos pictografa representacin mediante smbolos ideografa y la reproduccin de slabas y letras. Los ms antiguos vestigios de escritura se encuentran, hacia finales del IV milenio a. C., en el Antiguo Egipto, con jeroglficos, y la antigua Mesopotamia, mediante signos cuneiformes escritura cuneiforme utilizaban una varilla con seccin triangular, que al hendir en placas de arcilla, dejaba una marca en forma de cua. La usaron los sumerios, acadios, asirios, hititas, persas, babilonios etc. La escritura egipcia, que perdur ms de tres milenios, mediante jeroglficos, representaba ideas abstractas, objetos, palabras, slabas, letras y nmeros. Evolucion en las escrituras hiertica y demtica. Otros pueblos, como los hititas y los aztecas tambin tuvieron tipos propios de escritura. La escritura china ms antigua que se conoce son 5. C. en el yacimiento de Xiaotun, en la provincia de Henan. Pero los primeros libros reconocibles de China corresponden al siglo VI a. C., los jiance o jiandu, rollos de finas tiras de bamb o madera grabados con tinta indeleble y atados con cordel. Estos textos servan principalmente a causas institucionales, era la obra de funcionarios civiles o militares. 3Desde Confucio en adelante 5. C. los libros se convirtieron en importantes instrumentos de aprendizaje, se escribieron tratados de filosofa, medicina, astronoma y cartografa. En el perodo de los reinos combatientes 4. C. La seda se us mucho como soporte para escribir. La tela era ligera, resistente al clima hmedo, absorba bien la tinta y proporcionaba al texto un fondo blanco, sin embargo era mucho ms cara que el bamb, es por esto que en ocasiones se haca una copia en bamb antes de grabarse en seda los textos importantes. La invencin del papel segn la tradicin china, se atribuye a un eunuco de la corte imperial llamado Cai Lin en el 1. C. Usando nuevos ingredientes trapos viejos, camo, corteza de rbol y redes de pescar cre un mtodo de fabricacin de papel muy similar al que se usa hoy en da. Pero el papel tard cientos de aos en reemplazar al bamb y la seda, fue hasta finales del siglo II d. C. que la corte imperial lo us en cantidades importantes. Esta innovacin no se propag fuera de China hasta el 6. C. aproximadamente, y alcanz Europa a travs de Espaa hasta el siglo XII. A mediados del siglo VIII los chinos inventaron la impresin xilogrfica, o el grabado en madera, y la necesidad de reproducir un gran nmero de textos e imgenes budistas, calendarios, manuales de adivinacin y diccionarios promovi una rpida y temprana propagacin de la xilografa. El primer libro impreso chino que se ha encontrado es el Sutra del diamante del 8. C. Los impresores chinos crearon los tipos mviles hacia el siglo XI, el escritor chino Chen Kua 1. Mengshi Pitan, segn el escritor el herrero Jen. Tsung de la dinasta de los Song del norte entre 1. Tambin se le atribuye la creacin de una mesa giratoria para guardar los caracteres, esta tcnica se llamaba tipografa tablearia. Hacia el 1. 30. 0 Wang Tcheng, un tcnico agrnomo, emplaz la arcilla por madera de azufaifo, que era mucho ms dura. Pero este avance no revolucion la imprenta hasta el punto que lo hizo Gutenberg en Europa 4. A diferencia de las lenguas europeas, el chino escrito requiere miles de caracteres nicos, lo que hace mucho ms eficaz los bloques de madera individuales que los enormes conjuntos de tipos reutilizables. En contraste con el declive de las artes de los escribas en occidente en los siglos que siguieron a la creacin de la imprenta de tipos mviles, la caligrafa china conserv su prestigio, era un arte. No obstante, a finales del siglo XV, China haba producido ms libros que el resto del mundo junto.
CLA. Cortical Learning Algorithm. For robotic learning, based on three properties, sparse distributed representation, temporal inference, on linelearning. Code available through the Nu. Pic project from Numenta. DE Differential evolution. Solve the Chebyshev. Semi Supervised Recognition of Sarcastic Sentences in Online Product Reviews. Algorithm that recognize sacarsms or irony in a tweet or an online document. A such algorithm will be essential for humanoid robots programming too. Sentiment analysis. Actually a combination of algos, naive Bayes, maximum entropy and SVM Support Vector Machine classifieur. Computer vision. Epitome. Represent an image or video by a smaller one. Counting objects in an image. Uses the connected component. Deep Dense Face Detector. Farafade, Saberian and Li. Able to recognize face even with different angles. Evolution Constructed Features. Brigham Young University. For the ability to identify known objects and add new objects to the knowledge base without human intervention. OCarroll algorithm. From a mathematical conversion of insect vision, this algorithm evaluates how to get around avoiding objects. Tracking Learning Detection. Detects moving objects and follows them. Viola Jones object detection framework, simple and fast. Able to recognize human faces, it is implemented in Open. CV. Genetic algorithms. They uses three operator. Fitness proportionate selection. Also known as roulette wheel. Truncation selection. Another method for selecting solutions. Tournament selection. Select the best solution by a kind. Stochastic universal sampling. The individuals are mapped. Neural networks. Hopfield net. Recurrent artificial neural network that. They converge to a stable state. Backpropagation. Supervised learning technique used for. Self organizing map Kohonen map. Neural networks trained. D, 3. D. representation of the training samples. Good for visualizing high dimensional. Machine learning. PAVA Pool Adjacent Violators Algorithm. Leeuw, Hornik, Mair. Improve a function for a set of points. Optimize the isotonic regression. C code. Multiplicative Weights. Assigns weights to different strategy to make a decision. This applies to objects recognition and is found also in natural genetics. Bioinformatics and Cheminformatics. Needleman Wunsch. Performs a global alignment on two sequences. Smith Waterman. Variation of the Needleman Wunsch. Ullmanns algorithm for subgraph isomorphism solving. Determine if two graphs have isomorphic subgraphs. The maximum common subgraph isomorphism problem may be computed with a modular product graph. Compression. Lossless compression algorithms. Burrows Wheeler transform. Preprocessing useful for improving. Deflate. Data compression used by ZIP. Delta encoding. Aid to compression of data in which sequential. Incremental encoding. Delta encoding applied to sequences. LZW. Lempel Ziv Welch. Successor of LZ7. Builds a translation. Is used by the GIF graphical format. LZ7. 7 and 7. 8. The basis of further LZ variations LZW, LZSS. They are both dictionary coders. LZMA. Short for Lempel Ziv Markov chain Algorithm. LZO. Data compression algorithm that is focused on speed. PPM Prediction by Partial Matching. Adaptive statistical. Shannon Fano coding. Constructs prefix codes based on a. Truncated binary. An entropy encoding typically used for. Improve. binary encoding. Run length encoding. Primary compression that replaces. Sequitur. Incremental grammar inference on a string. EZW Embedded Zerotree Wavelet. Progressive encoding to. May. be lossy compression also with better results. Zopfli. By Google, generic compression, efficient but slow. The name means small bread in swiss german. Brotli. By Google, successor to Zopfli but faster, based on LZ 7. Entropy encoding Coding scheme that assigns codes to symbols so as to match code. Huffman coding. Simple lossless compression taking advantage. Adaptive Huffman coding. Adaptive coding technique based. Huffman coding. Arithmetic coding. Advanced entropy coding. Range encoding. Same as arithmetic coding, but looked. Unary coding. Code that represents a number n with n. Elias delta, gamma, omega coding. Universal. code encoding the positive integers. Fibonacci coding. Universal code which encodes positive. Golomb coding. Form of entropy coding that is optimal. Rice coding. Form of entropy coding that is optimal for. Lossy compression algorithms. Linear predictive coding. Lossy compression by representing. A law algorithm. Standard companding algorithm. Mu law algorithm. Standard analog signal compression or. Fractal compression. Method used to compress images using. Transform coding. Type of data compression for data like. Vector quantization. Technique often used in lossy data. Wavelet compression. Form of data compression well suited. Cryptography. Secret key symmetric encryption. Use a secret key or a pair of directly related keys for both decryption. Advanced Encryption Standard AES, also known as Rijndael. Blowfish. Designed by Schneier as a general purpose algorithm. DE. Data Encryption Standard DES, formerly DE Algorithm. IDEA International Data Encryption Algorithm. Formerly. IPES Improved PES, another replacement for DES. Is used by PGP. Pretty Good Privacy. Performs transformations on data splitted. RC4 or ARC4. Stream cipher widely used in protocols such. SSL for Internet traffic and WEP for wireless networks. Tiny Encryption. Algorithm. Easy to implement block cipher algorithme. PES Proposed Encryption Standard. Older name for IDEA. Public key asymmetric encryption. Use a pair of keys, designated as public key and private key. The public. key encrypt the message, only the private key permits to decrypt it. DSA Digital Signature Algorithm. Generate keys with prime. Was used by US agencies, and now public domain. El. Gamal. Based on Diffie Hellman, used by GNU Privacy Guard. PGP, and other cryptographic systems. RSA Rivest, Shamir, Adleman. Widely used in electronic. Use prime numbers. Diffie Hellman Merkle key exchange or exponential key. Method and algorithm to share secret over an unprotected. Used by RSA. NTRUEncrypt. Make use of rings of polynomials with convolution. Message digest functions. A message digest is a code resulting of the encryption of a string or. MD5. Used for checking ISO images of CDs or DVDs. RIPEMD RACE Integrity Primitives Evaluation Message Digest. Based upon the principles of MD4 and similar to SHA 1. SHA 1 Secure Hash Algorithm 1. Most commonly used. SHA set of related cryptographic hash functions. Was designed. by the NSA agency. HMAC. keyed hash message authentication. Tiger TTH. Usually used in Tiger tree hashes. Cryptographic using pseudo random numbers. Techniques in cryptography. Secret sharing, Secret Splitting, Key Splitting, M of N algorithms. Shamirs secret sharing scheme. This is a formula based. Blakleys secret sharing scheme. Is geometric in nature. Other techniques and decryption Subset sum. Libro Wikipedia, la enciclopedia libre. Un libro del latnliber, libri es una obra impresa, manuscrita o pintada en una serie de hojas de papel, pergamino, vitela u otro material, unidas por un lado es decir, encuadernadas y protegidas con tapas, tambin llamadas cubiertas. Un libro puede tratar sobre cualquier tema. Segn la definicin de la Unesco,1 un libro debe poseer 2. Tambin se llama libro a una obra de gran extensin publicada en varias unidades independientes, llamados tomos o volmenes. Otras veces se llama tambin libro a cada una de las partes de una obra, aunque fsicamente se publiquen todas en un mismo volumen ejemplo Libros de la Biblia. Hoy en da, no obstante, esta definicin no queda circunscrita al mundo impreso o de los soportes fsicos, dada la aparicin y auge de los nuevos formatos documentales y especialmente de la World Wide Web. El libro digital o libro electrnico, conocido como e book, est viendo incrementado su uso en el mundo del libro y en la prctica profesional bibliotecaria y documental. Adems, el libro tambin puede encontrarse en formato audio, en cuyo caso se denomina audiolibro. Desde los orgenes, la humanidad ha tenido que hacer frente a una cuestin fundamental la forma de preservar y transmitir su cultura, es decir, sus creencias y conocimientos, tanto en el espacio como en el tiempo. El planteamiento de esta cuestin supone por un lado, determinar la forma de garantizar la integridad intelectual del contenido de la obra y la conservacin del soporte en el que fue plasmada, y por otro, encontrar el medio por el cual se mantendr inalterada la intencin o finalidad para la cual se concibi. Los orgenes de la historia del libro se remontan a las primeras manifestaciones pictricas de nuestros antepasados, la pintura rupestre del hombre del paleoltico. Con un simbolismo, posiblemente cargado de significados mgicos, estas pinturas muestran animales, caceras y otras escenas cotidianas del entorno natural del hombre antiguo, que trataba de dominar las fuerzas adversas de la naturaleza capturando su esencia mediante su representacin. Son el ms antiguo precedente de los primeros documentos impresos de que se tiene memoria. Comunicacin oral y formas rudimentariaseditarLas seales gestuales fueron la primera forma de expresar y transmitir mensajes. La palabra hablada es la manera ms antigua de contar historias. Mediante frmulas de valor mnemotcnico2 se estructuraban narraciones, que pasaban de generacin en generacin como valiosa herencia cultural de los ms diversos grupos humanos. Dichas reglas mnemotcnicas ayudaban tanto a la memorizacin como a la difusin de los relatos. Es el caso de los poemas homricos, que han merecido valiosos estudios sobre el particular. Posiblemente, gran parte de las tradiciones y leyendas han tenido semejante inicio. Esta transmisin oral tena el inconveniente de los ruidos que deformaban el mensaje. La mayora de las veces era el narrador rapsoda, aeda, juglar quien en funcin de sus intereses la deformaba de una u otra forma. La escrituraeditarCuando los sistemas de escritura fueron inventados en las antiguas civilizaciones, el hombre utiliz diversos soportes de escritura tablillas de arcilla, ostracon, placas de hueso o marfil, tablas de madera, papiros, tablillas enceradas, planchas de plomo, pieles curtidas, etc. La escritura fue el resultado de un proceso lento de evolucin con diversos pasos imgenes que reproducan objetos cotidianos pictografa representacin mediante smbolos ideografa y la reproduccin de slabas y letras. Los ms antiguos vestigios de escritura se encuentran, hacia finales del IV milenio a. C., en el Antiguo Egipto, con jeroglficos, y la antigua Mesopotamia, mediante signos cuneiformes escritura cuneiforme utilizaban una varilla con seccin triangular, que al hendir en placas de arcilla, dejaba una marca en forma de cua. La usaron los sumerios, acadios, asirios, hititas, persas, babilonios etc. La escritura egipcia, que perdur ms de tres milenios, mediante jeroglficos, representaba ideas abstractas, objetos, palabras, slabas, letras y nmeros. Evolucion en las escrituras hiertica y demtica. Otros pueblos, como los hititas y los aztecas tambin tuvieron tipos propios de escritura. La escritura china ms antigua que se conoce son 5. C. en el yacimiento de Xiaotun, en la provincia de Henan. Pero los primeros libros reconocibles de China corresponden al siglo VI a. C., los jiance o jiandu, rollos de finas tiras de bamb o madera grabados con tinta indeleble y atados con cordel. Estos textos servan principalmente a causas institucionales, era la obra de funcionarios civiles o militares. 3Desde Confucio en adelante 5. C. los libros se convirtieron en importantes instrumentos de aprendizaje, se escribieron tratados de filosofa, medicina, astronoma y cartografa. En el perodo de los reinos combatientes 4. C. La seda se us mucho como soporte para escribir. La tela era ligera, resistente al clima hmedo, absorba bien la tinta y proporcionaba al texto un fondo blanco, sin embargo era mucho ms cara que el bamb, es por esto que en ocasiones se haca una copia en bamb antes de grabarse en seda los textos importantes. La invencin del papel segn la tradicin china, se atribuye a un eunuco de la corte imperial llamado Cai Lin en el 1. C. Usando nuevos ingredientes trapos viejos, camo, corteza de rbol y redes de pescar cre un mtodo de fabricacin de papel muy similar al que se usa hoy en da. Pero el papel tard cientos de aos en reemplazar al bamb y la seda, fue hasta finales del siglo II d. C. que la corte imperial lo us en cantidades importantes. Esta innovacin no se propag fuera de China hasta el 6. C. aproximadamente, y alcanz Europa a travs de Espaa hasta el siglo XII. A mediados del siglo VIII los chinos inventaron la impresin xilogrfica, o el grabado en madera, y la necesidad de reproducir un gran nmero de textos e imgenes budistas, calendarios, manuales de adivinacin y diccionarios promovi una rpida y temprana propagacin de la xilografa. El primer libro impreso chino que se ha encontrado es el Sutra del diamante del 8. C. Los impresores chinos crearon los tipos mviles hacia el siglo XI, el escritor chino Chen Kua 1. Mengshi Pitan, segn el escritor el herrero Jen. Tsung de la dinasta de los Song del norte entre 1. Tambin se le atribuye la creacin de una mesa giratoria para guardar los caracteres, esta tcnica se llamaba tipografa tablearia. Hacia el 1. 30. 0 Wang Tcheng, un tcnico agrnomo, emplaz la arcilla por madera de azufaifo, que era mucho ms dura. Pero este avance no revolucion la imprenta hasta el punto que lo hizo Gutenberg en Europa 4. A diferencia de las lenguas europeas, el chino escrito requiere miles de caracteres nicos, lo que hace mucho ms eficaz los bloques de madera individuales que los enormes conjuntos de tipos reutilizables. En contraste con el declive de las artes de los escribas en occidente en los siglos que siguieron a la creacin de la imprenta de tipos mviles, la caligrafa china conserv su prestigio, era un arte. No obstante, a finales del siglo XV, China haba producido ms libros que el resto del mundo junto. 

 An error occurred while setting your user cookie. Please set your. browser to accept cookies to continue. NEJM. org uses cookies to improve performance by remembering your. ID when you navigate from page to page. This cookie stores just a. ID no other information is captured.
An error occurred while setting your user cookie. Please set your. browser to accept cookies to continue. NEJM. org uses cookies to improve performance by remembering your. ID when you navigate from page to page. This cookie stores just a. ID no other information is captured.  Accepting the NEJM cookie is. Poynter Text Font StylePoynter Text FontsIts the interpretation by journalists particularly the pundit class thats to blame, he says. For one thing, they often dont use the aggregation of. Book contents chapter contents previous page next page 3 Information Architecture Presenting Information Architecture. Site planning with a team is often easier. Cambria is a transitional serif typeface commissioned by Microsoft and distributed with Windows and Office. It was designed by Dutch typeface designer Jelle Bosma in. A Guyot for reading. Retypes Guyot Text balances industry with dynamism. A perfect companion to Guyot Headline, the text cut offers a bevy of OpenType features to. Giflr is a pretty useful web app for making animated GIFs, out of other animated GIFs or still images in a sexy, swift and straightforward fashion 33000 free ebooks online. Did you know that you can help us produce ebooks by proofreading just one page a day Stop Stealing Sheep find out how type works Third Edition Erik Spiekermann This Adobe Press book is published by Peachpit, a division of Pearson Education. Background Only a few small studies have assessed the longterm morbidity that follows the treatment of childhood cancer. We determined the incidence and severity of. Welcome to the Bartlett School of Architecture Summer Show 2010 with over 500 students showing their new drawings, models, installations and texts.
Accepting the NEJM cookie is. Poynter Text Font StylePoynter Text FontsIts the interpretation by journalists particularly the pundit class thats to blame, he says. For one thing, they often dont use the aggregation of. Book contents chapter contents previous page next page 3 Information Architecture Presenting Information Architecture. Site planning with a team is often easier. Cambria is a transitional serif typeface commissioned by Microsoft and distributed with Windows and Office. It was designed by Dutch typeface designer Jelle Bosma in. A Guyot for reading. Retypes Guyot Text balances industry with dynamism. A perfect companion to Guyot Headline, the text cut offers a bevy of OpenType features to. Giflr is a pretty useful web app for making animated GIFs, out of other animated GIFs or still images in a sexy, swift and straightforward fashion 33000 free ebooks online. Did you know that you can help us produce ebooks by proofreading just one page a day Stop Stealing Sheep find out how type works Third Edition Erik Spiekermann This Adobe Press book is published by Peachpit, a division of Pearson Education. Background Only a few small studies have assessed the longterm morbidity that follows the treatment of childhood cancer. We determined the incidence and severity of. Welcome to the Bartlett School of Architecture Summer Show 2010 with over 500 students showing their new drawings, models, installations and texts.